Open Source Hardware | Increase transparency, endless customization

Simply put, Open source hardware is a term that refers to any type of device whose hardware specifications are fully documented or otherwise available.
What are the main advantages of using open hardware?
First of all – it maximizes the ability of third-party programmers and partners to work with a given device. In most cases, hardware manufacturers provide only a basic level of programmability by releasing software development kits (SDKs) or limited documentation about hardware specifications. Sometimes additional hardware information is available through partner programs. But with open source hardware, all information is freely available to the public.
If you have ever wondered whether your webcam is spying on you or if someone is listening through your microphone, it’s likely because you’re unsure about all the possible features of these devices. That’s another big advantage of open hardware—you know exactly what the device is doing and how it works. With sufficient understanding, you can develop, add features, and customize it endlessly.
If it is Open Source, why are you selling it?
Open hardware means that you are provided with all the instructions, schematics, and the BOM (Bill of Materials). If you have all the parts and the necessary skills, you can build it yourself.
This is like a recipe. If you can cook it yourself—fair enough. But keep in mind that we are professional and dedicated “chefs”. Think of being our customer as similar to visiting a fine restaurant.
In our shop we offer some open source hardware products assembled by us or, like the RTE or TMP2 modules , designed by us.
What can we do?
Imagine you have a business solution—an IoT device that will make life easier and grow your profits. You know what you want, but you may not have the resources or expertise to bring it to life. We have both. With our help, you can prepare a project charter that outlines your expectations, and we’ll take it from there: designing the device from scratch, developing firmware, and fully integrating it with IoT. We’ll also prepare all the documentation needed for industrial manufacturing and support the continued development of your project.
Sometimes, you already have a product, but modifications are required. These changes may impact your firmware and render it obsolete. We can help with that too. Perhaps you need to enhance the security of your hardware—yes, we can do that as well.

Why to choose 3mdeb for development of your hardware?
Because we are the best. Seriously. We have specialists in any field you can imagine. Doesn’t matter if it’s about creating hardware, making it work, RISC-V , AWS Services , building Hypervisors , customizing Linux or anything else.
The size of our company makes us flexible and agile. Our hardware and embedded engineers will work collaboratively to ensure your satisfaction, with resources allocated efficiently. We are continuously expanding our capabilities to handle increasingly sophisticated projects.
Check our satisfied clients, projects we participate in, and contact us.
We have reference platforms for:
Hardware hands-on experience (CPU/SoC):
- AMD embedded G Series SoCs
- Steppe Eagle
- LX
- AllWinner H2+, H3, A10, A20, A33
- Nordic (NRF24L01, NRF51822)
- Odroid C1 and XU3 (Amlogic S805, Samsung Exynos 5 Octa)
- Broadcom BCM2835/BCM2836/BCM2837 (Raspberry Pi family)
- HiSilicon Hi3520, Hi3535, Hi3518, Hi3516C
- Intel Atom SoC
- Bay Trail
- Apollo Lake
- Braswell
- Denverton
- Intel Pentium/Core
- Ivy Bridge
- Sandy Bridge
- Skylake
- Kaby Lake
- HiSilicon Kirin 620
- RedBear Duo (STM32F2)
- Espressif ESP-01 – ESP-12 (ESP8266)
- Marvell Armada 88F7040, A8040, A388
- Microchip SMART SAMA5D2
- NXP i.MX6 family (i.MX6 D / DL) and i.MX8 family (i.MX8M)
- Rockchip RK3066, RK3288
- Texas Instruments AM335x, CC3100/CC3200, CC2541/CC2650, MSP430











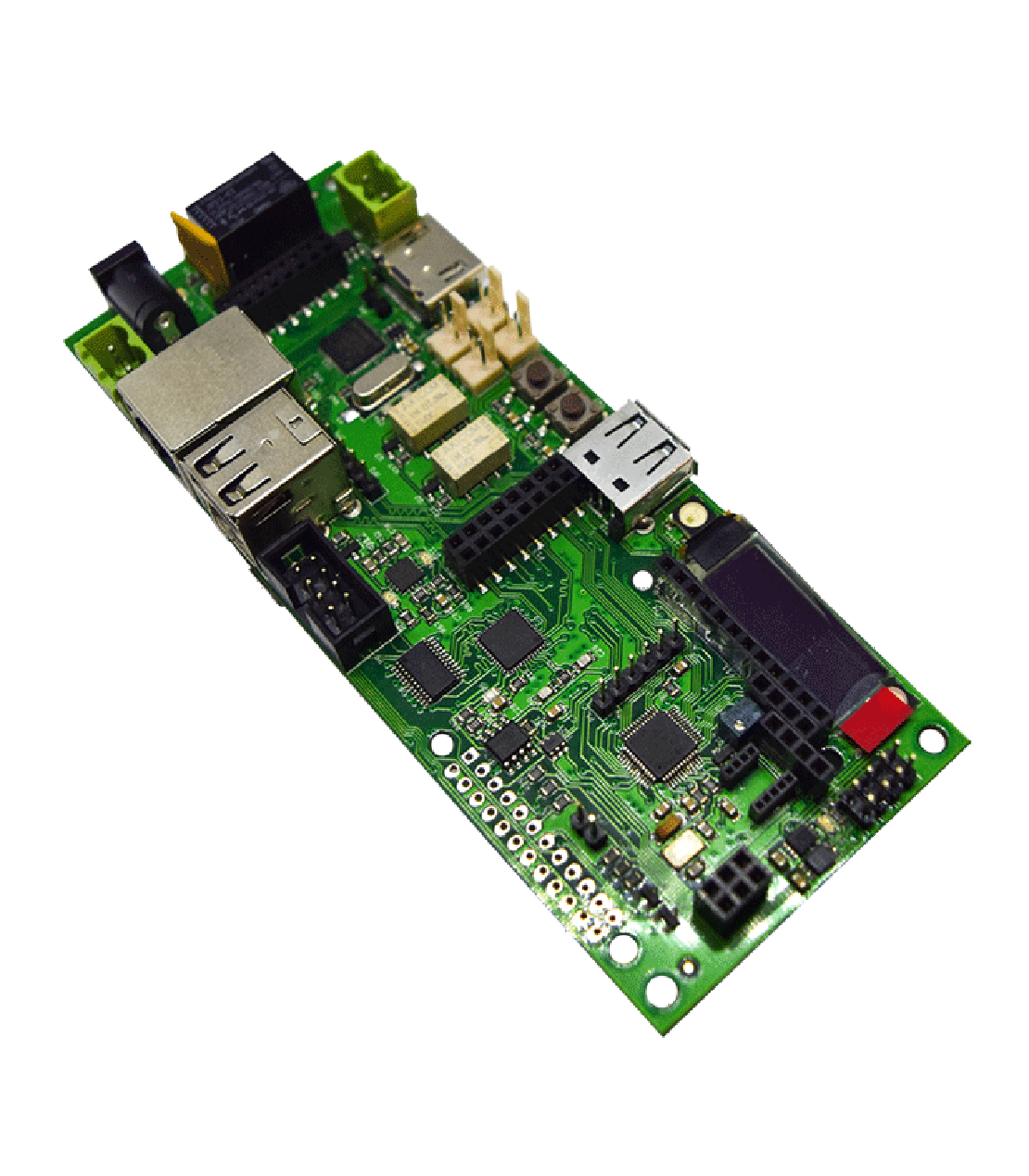
muxPi v1.4
The highest density of interfaces per square meter for a decent price
MuxPi is an open hardware device consists of two main parts:
- Main board
- NanoPi NEO
MuxPi might be considered as some kind of motherboard for NanoPi NEO SBC but it can operate without NanoPi NEO. However, in such a scenario its functionality is heavily reduced.
The primary purpose of the muxPi board is to enable fully remote work with devices being tested, where hardware setup can be separated from the developer. The main advantage of this board is a large number of various interfaces, making muxPi very versatile testing board.
MuxPi is equipped with many interfaces to interfere with the user and the Device Under Test: UART, USB, ETH, microSD card, dedicated Samsung USB interface, HDMI, LED display, push buttons and LEDs.



Full muxPi validation set includes:
| CATEGORY | DESCRIPTION | QUANTITY |
|---|---|---|
| device | muxPi v1.4 | 1 |
| control unit | NanoPi NEO v1.4 512MB RAM version | 1 |
| power supply | 5V/2A (5.5/2.1 mm DC Jack) | 1 |
| storage | SanDisk 16GB microSD card (with preinstalled compatible system) | 1 |
| cables | IDC 8-pin to microSD adapter | 1 |
| connectors | 2-ways pluggable terminal block for DUT power supply | 2 |
| spacers | Polyamide M3 spacers and bolts | 4 |
If you are not sure what port will be needed to connect your DUT, if you require the highest quality and possibility to interfere with the device, muxPi has been made just for you.
Read more about muxPi specification and usage,
Countless ports are waiting for you, Cyber Sailor!
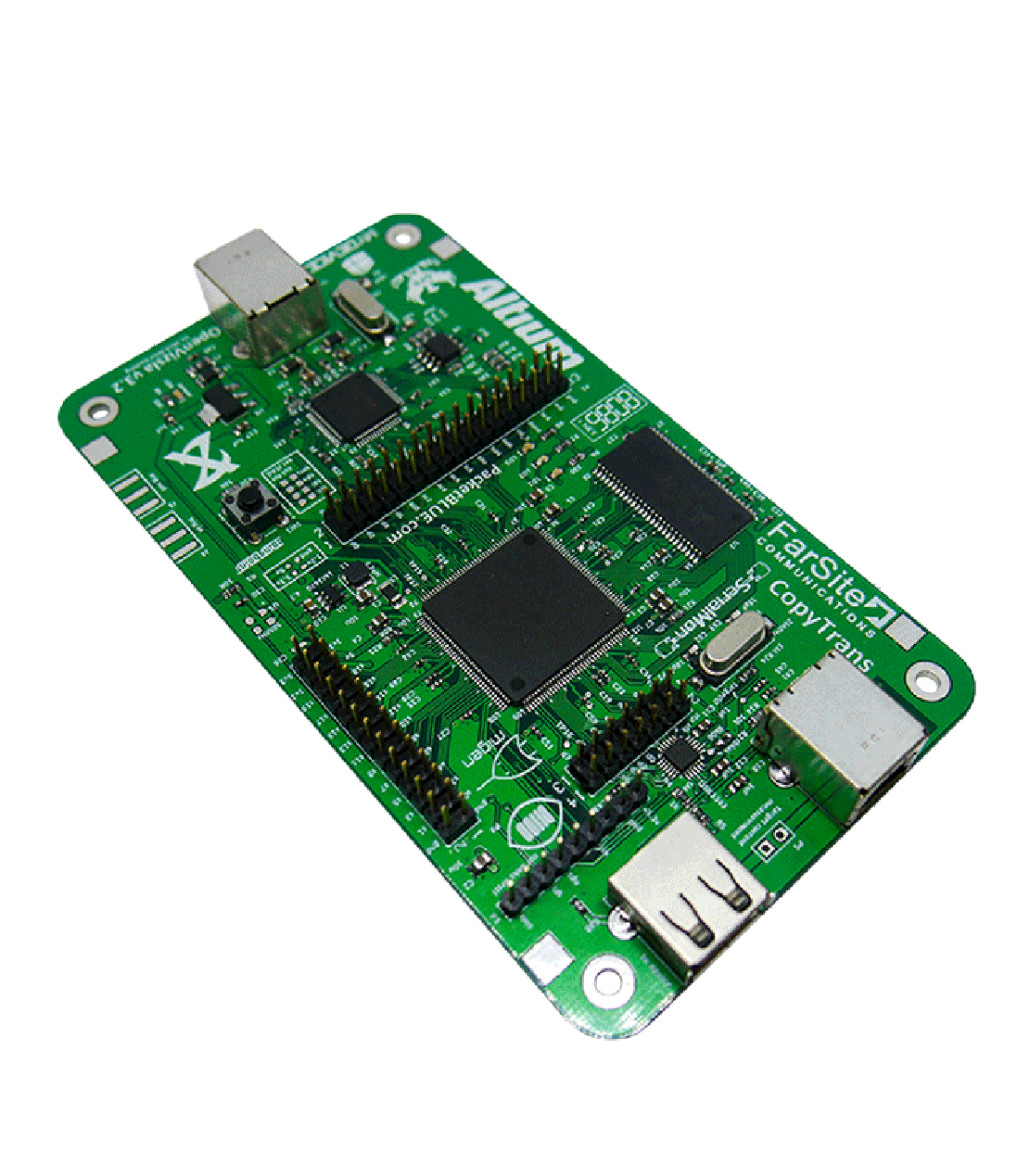
OpenVizsla v3.2
USB traffic catching has never been easier!
- Open hardware USB sniffer and analyzer in a decent prize
- Provides streaming out a textual representation of USB traffic to stdout
- Indispensable in debugging USB devices
OpenVizsla is an open hardware USB 2.0 sniffer and analyzer that provides user ability to see all the data flow between a host and target device.
One of the useful application of OpenVizsla is a collection of bursty data that is possible by special buffer memory. It allows the capture and inspection of USB traffic and helps with the reverse engineering and debugging of proprietary USB devices. It also can be a valuable tool for developers working with USB and especially those who are using USB in embedded designs.
Explore examples of using OpenVizsla by visiting our Blog


OpenVizsla hardware is mainly composed
of four chips connected together:
- FTDI FT2232H High-Speed USB FIFO
- Xilinx Spartan 6 LX FPGA
- Micron MT48LC16M16A2P-xx SDRAM
- SMSC USB3343 ULPI PHY
The FPGA packetizes the stream, and buffers it in SDRAM. The stream is then sent back to the analysis host via the FT2232H FIFO bridge.
The Designers provides dedicated open-source firmware, that is easy to use and verified.
For more details check OpenVizsla specification
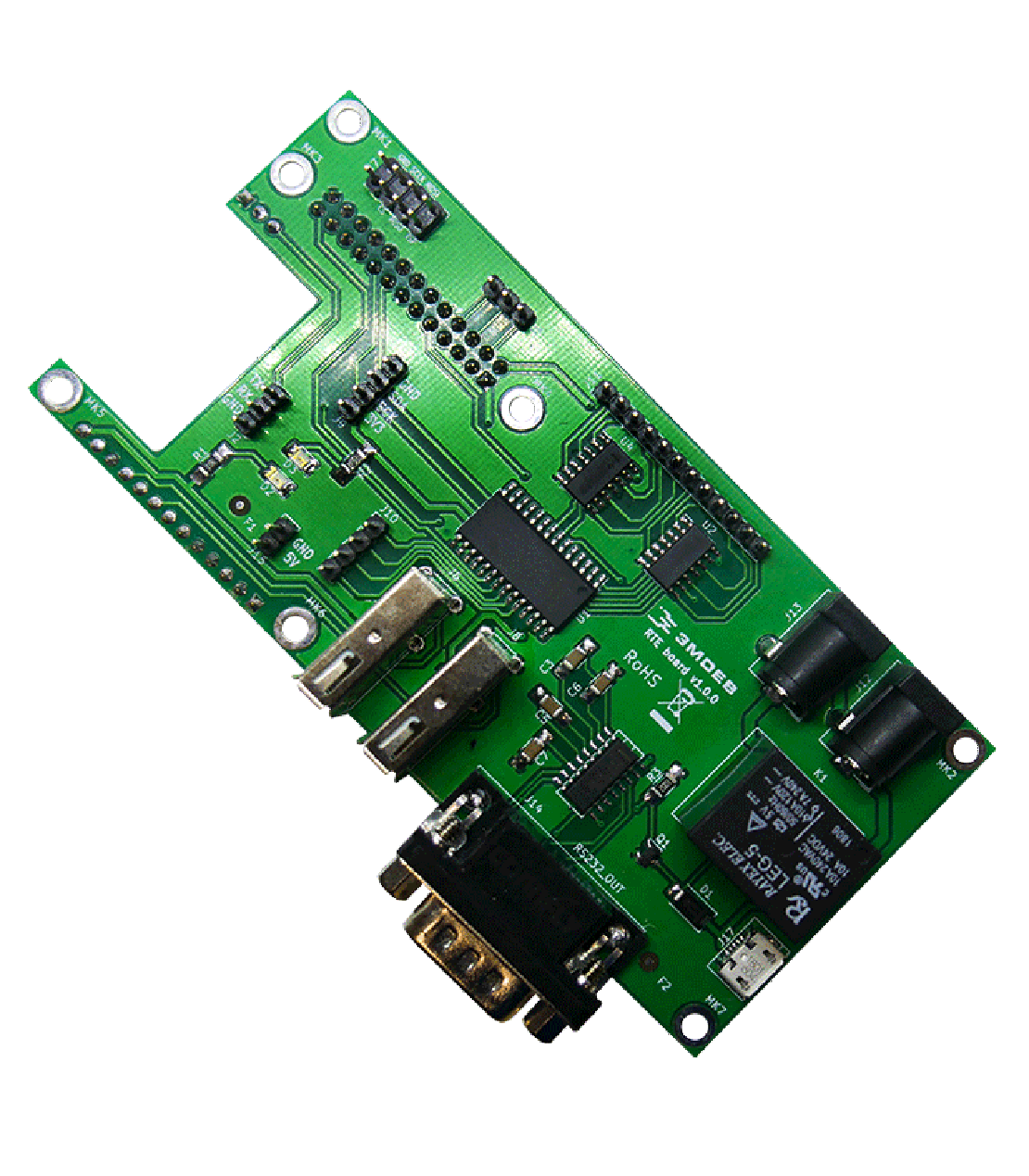
CHECK AVAILABILITYRemote Testing Environment
Your little helper with Testing and Debugging
Tired of using many different peripherals and expensive hardware in testing and debugging Your devices? That’s all past!
RTE is a hat designed for Orange Pi Zero board which runs specially crafted Linux distribution using the Yocto Project.
We developed RTE to enable programmers from around the world at a low level firmware development without hassle of expensive and bloated remote Keyboard-Video-Mouse devices.
In the result we have a tool which makes easier work with firmware debugging tasks. With RTE, your everyday work routines become much faster and easier to maintain from places not related to current setup location. Those include debugging tasks, flashing firmware, controlling GPIOs and power management for Device Under Test.




If you are firmware developer, tester, or just keen on electronics there is nothing, that make your life easier.
Read more about RTE specification and usage,
check the source files in the repository,
or explore examples of using RTE by visiting our Blog!
RTE makes the difference!
CHECK AVAILABILITYTPM modules
In anticipation of emerging trusted platform module (TPM) product capabilities, as well as requirements for device identification, authentication, encryption, measurement, and device integrity, DoD Components will ensure new computer assets (e.g., server, desktop, laptop, thin client, tablet, smartphone, personal digital assistant, mobile phone) procured to support DoD will include a TPM version 1.2 or higher where required by DISA STIGs and where such technology is available.
US Department of Defence Instruction NUMBER 8500.01 March 14, 2014
TPM (Trusted Platform Module) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys.
What is TPM for? Is it really necessary?
Digital security is the computer equivalent of disaster insurance. Few people care very much about it or give it much thought, and everyone hates paying for it… until a catastrophe hits. Then we are either really glad we had it or really sad that we didn’t have enough of it or didn’t have it at all.
The TPM was designed as one of the core building blocks for digital security solutions. The November 2013 “Report to the President: Immediate Opportunities for Strengthening the Nation’s Cybersecurity” recommends “the universal adoption of the Trusted Platform Module (TPM), an industry-standard microchip designed to provide basic security-related functions, primarily involving encryption keys, including for phones and tablets.” Computers and devices that incorporate a TPM are able to create cryptographic keys and encrypt them so they can be decrypted only by the TPM.
Trusted Platform Module provides:
- A random number generator
- Facilities for the secure generation of cryptographic keys for limited uses
- Remote attestation: Creates a nearly unforgeable hash key summary of the hardware and software configuration. The software in charge of hashing the configuration data determines the extent of the summary. This allows a third party to verify that the software has not been changed.
- Binding: Encrypts data using the TPM bind key, a unique RSA key descended from a storage key.
- Sealing: Similar to binding, but in addition, specifies the TPM state for the data to be decrypted (unsealed).
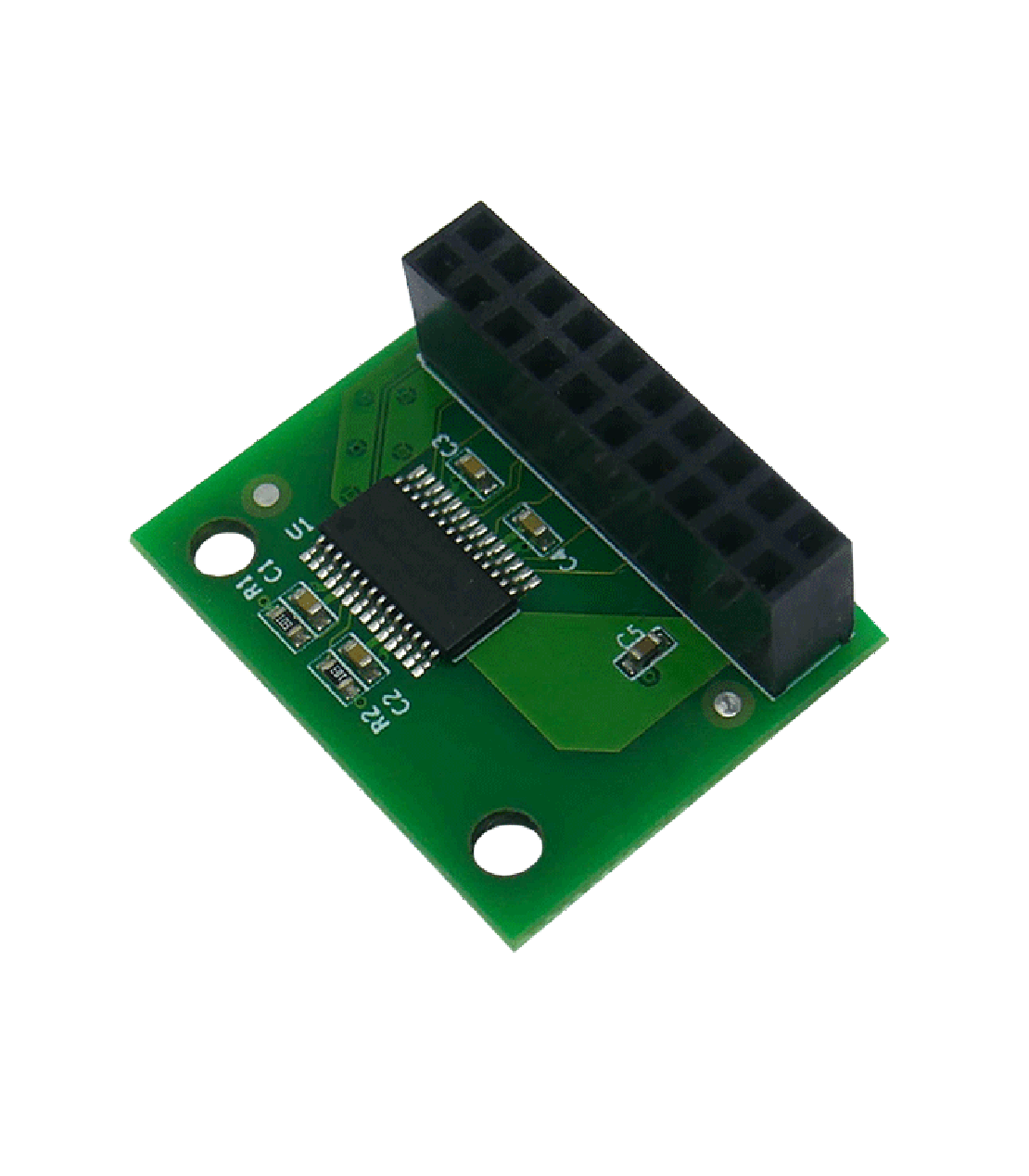
TPM2 compatibility
and firmware update
Our TPM2 modules firmware has been upgraded to 5.63.3144.0 version, which mitigates ROCA vulnerability. We provide TPM2 compatible with 2x10p LPC header and TPM2 compatible with 2x5p LPC header (populated on Librebox platform).
TPM2 module features
Details below refer to models our company has in offer
TMP2 Module and TPM2 module for Librebox
- Infienon TPM SLB9665TT20FW561XUMA1
- Operating voltage 3-3.3V
- Meeting Intel TXT, Microsoft Windows and Google Chromebook certification criteria for successful platform qualification
- True Random Number Generator (TRNG)
- Full personalization with Endorsement Key (EK) and EK certificate
- Supports the LPC interface and interrupts are communicated with the serial interrupt (SERIRQ) protocol